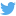
By then international media reported that three people were killed after troops opened fire.
During the 1st of August 2018, we monitored and recorded how Zimbabwe Electoral Commission (ZEC) website was defaced. The defacement was widely reported in the local media and social media.
Minutes after the website administrators using a functionality of the control panel took the content of the website offline. The link /cgi-sys/suspendedpage.cgi is common from Cpanel Control Panel
At a press briefing on Thursday, 2nd of August 2018 the ZEC Commissioner Qhubani Moyo said they were forced to temporarily stop the site (…) because hackers started uploading “pictures” which the poll management authority did not know about and that they could not disclose what sort of information had been posted. Moyo also stated that the website security was improved after the attack.
The defacement
As far as we know, all the media coverage of this security event has been re-using one single screenshot of the defacement and such capture does not include the full content of the homepage.
Although Qhubani Moyo claimed that the website was cleaned and recovered quickly, by the 3rd of August 2018, we could still verify that the defacement remained hosted in the website with the name “indexhacked.php“.
The page included images that were uploaded to the platform twimg.com.

Pictures of the defacement includes a picture of Emmerson Mnangagwa and Jeff Flake https://twitter.com/JeffFlake who made statements of how good were the elections ignoring the 1st Aug events.
A copy of the defacement is available in the archive site here
The page changed around 18.20 PM, the 1st of August 2018.
Qhubani Moyo’s full statement reads:
Yesterday some hackers attacked our website and posted some pictures that were not from Zec. At exactly 11 minutes from the development, we decided to pull down the website so that we avoid spreading false hoods that were being spread by hackers on the Zec website. We are working on reconstructing it and this time it will be more secure. I don’t know why they did it and I will not get deeper into how we will secure it and it is safer to say it will be up soon. Our technical teams are seized with the matter and they are investigating so we find out what really happened. We’ll also trace where the hackers originate from so we catch the political criminal elements.
The defacement code
The defacement page contains the following four obvious signatures:
<!-- A hero with no name --> Z.E.C - Hacked by the victims of ZANU-PF Contact us on Twitter @zim4thewin .Join the fight against tyrany. Z.E.C - Hacked by Team Pachedu
It is obvious that the defacer left enough hints to attribute the attack and the motivations.
Who is @zim4thewin?
zim4thewin aka xⒶzy is a digital activist active in Africa that claimed the denial of service attacks against the South African SABC back in 2016 to ban the filming of violent protests.
More details about @zim4thewin and Anomymous Africa can be found here and here
Who is Team Pachedu?
The defacer included a reference to “Team Pachedu“, a civil society interdisciplinary team that has raised concerns about the 2018 voters’ roll, with sufficient evidence of human manipulation. Their reports are available at the site http://www.teampachedu.org and https://thiscitizen.org/
It is unclear what connection @win4thewin has with the Team Pachedu but it is likely that the defacer is just endorsing their work rather than being a formal member.
Is the website still compromised?
As a result of the experience we have gained auditing websites, we have developed several in-house techniques to identify the presence of stealth backdoors.
Just a few hours after the defacement, we found the presence of a backdoor inside the unprotected area of the admin area.
The backdoor seems to make use of the data send in the Website referer HTTP_REFERER and Accepted Language Header (HTTP_ACCEPT_LANGUAGE) to initialize an interactive session. When we saw that behavior we thought immediately in “Weevely”, a PHP backdoor that is part of Kali Linux.
A detailed analysis of the backdoor is here and here
More info of Weevely and Kali Linux is documented here
The unprofessional website security of ZEC
This is what we know of the ZEC website and why we believe the website does not meet basic security standards.
- Customized code: The site is not using any development framework and it is totally customized.
- Limited international bandwith: The site is hosted at 41.57.65.19 at Africom ai.co.zw AS36986
- Poor admin authentication: Authentication to the admin area relies on poorly written and insecure bad Javascript code.
- Shared hosting: The website is in a shared hosting with other sites, namely: netguardsec.com, guroohosting.ai.co.zw and chisipoconsultants.co.zw

- Poor sanitation of data input: The download functions in the unprotected admin area of the site lack proper input sanitation allowing an attacker to download and upload any files to the server.
- No advance firewall: No proper firewall or session rate control is in place, allowing the attacker to brute force the admin password. No intrusion detection system is in front of the website, allowing SQL injection and illegitimate GET/POST commands.
- Poor code development: Poor development practices, the developer left old copies of files and backup copies.
Conclusions
- Although it is difficult to attribute a cyberattack, our forensic investigation confirms that the website was defaced the evening of the 1st of August 2018 and the attack was claimed using the nick zim4thewin
- That the motivations of the attack are clearly expressed by the defacer: protest against the military actions taking place in the streets.
- That the intruder most probably exploited the very poor security of the Zimbabwe Electoral Commission (Javascript and admin area) code and uploaded a stealth backdoor to keep persistent access to the website.
- The poor website security of the site does not conform to state of the art security standards and best practices.
- An experienced pen tester could identify the flaws all the website within hours and that makes us believe that the website never underwent any security audits.
- That once the website was put backonline, we could not identify any substantial improvements in the website security.
Media
[Aug 3, 2018] Daily News, Electoral Commission website hacked,
[Aug 2, 2018] The Zambian Observer, Zimbabwe Election Commission confirms site hack
[July 24, 2018] Mail & Guardian, Even before the vote, Zimbabwe’s election is not credible
[July 19, 2018] Sunday Times, The Elders descend on Zimbabwe ahead of crucial elections
[July 12, 2018] Daily News, Hackers downloaded voters’ personal data
APPENDIX
How did we know that weevely was used by the attacker?
In order to keep control of the server, zim4thewin left a copy of weevely backdoor in the server.
The weevely server side code looks like this
Without entering into much technical details about the webshell obfuscation technique, the webshell relies on messages exchange between the attacker and the webserver side that are transmitted using the HTTP_REFERER and HTTP_ACCEPT_LANGUAGE HTTP headers.
An carefully analysis of Weevely server side code reveals that independently of knowing the “credentials” to access the backdoor, a cookie (session) starts when the HTTP_REFERER and HTTP_ACCEPT_LANGUAGE are sent.
Looking for index pages that return cookies under these conditions reveal the possible presence of the backdoor.
<snip>
$r = $_SERVER;
$rr = @$r["HTTP_REFERER"];
$ra = @$r["HTTP_ACCEPT_LANGUAGE"];
if ($rr && $ra) {
$u = parse_url($rr);
parse_str($u["query"], $q);
$q = array_values($q);
preg_match_all("/([\w])[\w-]+(?:;q=0.([\d]))?,?/", $ra, $m);
if ($q && $m) {
@session_start(); // Session starts (cookie) only when HTTP_REFERER and HTTP_ACCEPT_LANGUAGE are sent
</snip>
If you are interested to know more about weevely webshell, you can watch this very good presentation here for more details.
Post published in: Featured